In today’s digital world, strange words like binopofizxoc sometimes show up in website links, error messages, or computer code. It looks confusing, but it might just be a random code or a test word used by developers.
Some people think it could be part of a hidden tool or system. It’s not clear what it really means, but it’s important to know if it is safe or not. Seeing such words can make people curious or even worried. This article will explain binopofizxoc in simple words to help you understand it better.
What Is Binopofizxoc?
Binopofizxoc is a machine-generated digital identifier often encountered in URLs, software code, or error logs. It typically appears as a random alphanumeric string, used for temporary tracking, internal labeling, or debugging purposes.
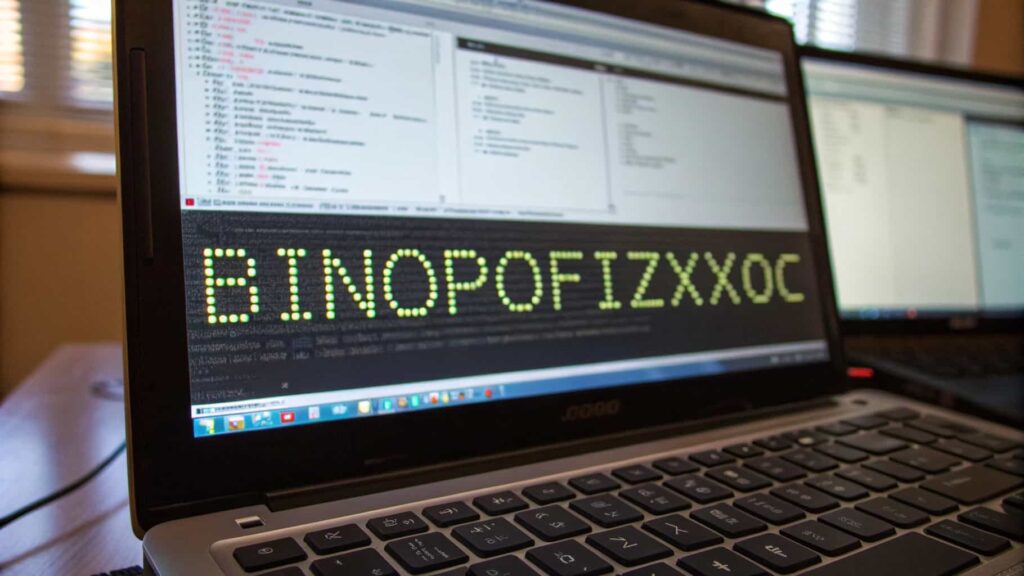
While it may seem mysterious, such terms are usually benign and part of standard system operations. In some cases, they can help identify issues during software development or system processes. Users should stay cautious but not overly concerned, as these identifiers are rarely associated with malicious activity.
Why Are People Searching For Binopofizxoc?
People are searching for “binopofizxoc” due to its mysterious appearance in system messages, browser histories, or as part of unfamiliar code. This term could be linked to beta testing, internal project identifiers, or even malware components.
Users often look it up out of curiosity or concern about its role in their devices. Additionally, it might be an obscure label used in software or cybersecurity systems for security or version control purposes. Searches often arise when it appears unexpectedly, raising questions about its safety and function.
What Are The Potential Meanings Behind Binopofizxoc?
When dissecting the potential significance of binopofizxoc, it is helpful to view the term through different lenses. Experts consider various possibilities based on where and how such terms are typically encountered in the digital ecosystem.
Software Or AI Project Designations:
One of the prevailing theories is that binopofizxoc represents a temporary name or code for an internal software or artificial intelligence project. Within organizations:
- Project Codenames: Firms often assign code names to experimental projects or in-development features, and these names sometimes leak through beta releases or system logs.
- AI Modules: Artificial intelligence systems, known for creating iterative data, may use such identifiers as a part of their internal language model testing or for labeling distinct functionalities.
Hidden Malware Or Spyware Components:
Cybersecurity professionals occasionally encounter strings like binopofizxoc hidden deep within malicious software code. In this context, the term could be:
- A Concealed Command Identifier: Often used by hackers to relay commands within malware.
- A Fragment of an Encryption Key: Part of obfuscated code to hide malicious activities from simple scans.
- Component of a Command-and-Control (C2) Server Address: Helping malicious software to connect with its backend operators.
While these possibilities can seem alarming, it is essential to remember that the mere presence of binopofizxoc does not confirm malicious intent.
Machine-Learned Terminology And Test Cases:
With the advancement of machine learning and AI, algorithms are often tasked with generating and processing vast amounts of data. This process sometimes results in:
- Machine-Generated Words: Unique combinations of letters like binopofizxoc are sometimes output as part of training test cases.
- Fake Data Labels: In testing scenarios, AI systems might create labels and temporary identifiers that inadvertently appear in public logs.
- Simulated Data Sets: These identifiers help verify the behavior of new systems before adopting official nomenclature.
This interpretation supports the idea that binopofizxoc is not a deliberate attempt at obfuscation but rather an artifact of a system that operates on machine-generated data.
Code Snippets, Variables, And Configuration Keys:
Another practical origin for binopofizxoc may be as a random value inserted into the code:
- Variable Names: Developers sometimes use auto-generated names when the exact functionality might still be under review.
- Configuration Tokens: These strings are used in configuration files or API keys, serving as placeholders or temporary tokens.
- Debugging Placeholders: In coding, certain terms are used temporarily during debugging and testing phases and may end up in user-facing logs unintentionally.
Each of these possibilities outlines a non-threatening scenario where binopofizxoc serves a utilitarian purpose within software development.
When Does Binopofizxoc Appear In Your Digital Life?
Binopofizxoc can appear in different digital scenarios, including URLs, browser histories, and software code. It often shows up in encrypted or temporary links, third-party tracking systems, or cached data in your browser. In software development, it may appear in debug logs or as a temporary tag used during testing.

System errors or logs can also display this term, often as part of error reporting or diagnostics. If you come across it in a URL or code, avoid interacting with unknown links and ensure they’re from trusted sources. For developers or tech-savvy users, reviewing the context in error logs is crucial. Consult IT professionals if you’re uncertain to prevent potential vulnerabilities or security concerns.
Should You Be Concerned? – Safety Measures Related To Binopofizxoc!
If you encounter “binopofizxoc,” it’s important to identify its source. Check URLs with trusted scanners to ensure they are safe, and examine software logs to see if it’s a development artifact. If it appears in error messages, document the full context and research it further.
Protect your device by scanning with antivirus tools and clearing browser data. Keep all software updated to avoid vulnerabilities. If concerns persist, consult with IT support or cybersecurity experts. Engaging with tech communities can also provide valuable insights for resolution.
Managing Unexpected Appearances Of Binopofizxoc – Key Steps!
Proactive Device Scanning:
Regularly scan your devices with trusted antivirus software like Malwarebytes, Bitdefender, or Kaspersky. Schedule periodic checks, especially if you encounter unfamiliar terms like binopofizxoc. Review scan reports for any alerts and take appropriate action. Keeping your system updated can prevent future issues.
Understanding And Analyzing Error Logs:
Use advanced log analysis tools to detect abnormal patterns linked to binopofizxoc. Engage IT professionals to interpret error logs and ensure no issues are missed. Comparing logs with past data can reveal if the term has appeared before. It helps to track whether it’s part of a recurring issue.
Leveraging Community Knowledge And Forums:
Tech forums like Stack Overflow and LinkedIn groups offer valuable insights on terms like binopofizxoc. By sharing your experience, you can gain clarity and learn from others facing similar challenges. Collaborating with the community helps identify potential risks and solutions.
What Is Binopofizxoc’s Role In Cybersecurity And Ethical Hacking?
Terms like binopofizxoc serve as early warning signs in cybersecurity, signaling potential security breaches. Their presence in suspicious files or logs highlights the need for advanced monitoring systems.These identifiers contribute to threat intelligence by improving anomaly detection.
Ethical handling involves respecting privacy and adhering to responsible disclosure protocols. Educating users about these terms reduces panic and fosters understanding. Maintaining ethical integrity is key to ensuring a safer digital environment.
How Does Binopofizxoc Compare To Other Similar Digital Terms?
binopofizxoc is one of many random alphanumeric strings used in digital systems for specific functions like device identification or process management. Similar terms include YT5683UX (Wi-Fi signal traces) and Xxha009 (background operations). Cybersecurity experts note these identifiers are often non-threatening unless associated with suspicious activity.
While they are common in encrypted URLs and software code, further investigation is recommended when they appear in unusual contexts. The rise of machine-generated identifiers like binopofizxoc reflects evolving digital security practices. Understanding these terms can help users differentiate between benign occurrences and potential threats.
What Is The Future Of Binopofizxoc In A Rapidly Evolving Digital Ecosystem?
As digital ecosystems evolve, greater transparency will be introduced, with companies explaining identifiers like binopofizxoc in system notifications. Machine-generated terms will integrate into next-gen technologies like blockchain, IoT, and AI for better system management.

Regulatory bodies may enforce data protection policies, establishing standards for these identifiers. Industry-wide practices will promote safer and more standardized digital operations. Transparency, security, and compliance will be crucial in safeguarding user data and improving system integrity.
FAQ’s
What Does Binopofizxoc Mean?
Binopofizxoc is a random, machine-generated identifier often used in system logs, URLs, or as part of internal tracking. It doesn’t have a specific meaning but serves as a placeholder or a temporary reference. These types of terms are common in software development and debugging.
Is Binopofizxoc A Security Threat?
Binopofizxoc by itself is not a security threat. It’s typically used for tracking or identifying specific components in a system. However, if it appears in suspicious contexts, further investigation is recommended to rule out any potential security risks.
How Can I Identify If Binopofizxoc Is Linked To Malware?
If binopofizxoc appears in unusual files, unknown URLs, or system errors, it might be worth scanning your device with trusted antivirus software. Additionally, reviewing the context of its appearance can help determine if it’s part of a legitimate process or potential malware activity.
Why Does Binopofizxoc Appear In Error Logs?
Binopofizxoc may show up in error logs as part of a system’s debugging process. These identifiers are used internally by developers to track errors and issues without revealing sensitive information. It’s a standard practice in troubleshooting and doesn’t necessarily indicate a problem.
Can Binopofizxoc Appear In Blockchain Or Iot Systems?
Yes, binopofizxoc-like identifiers may appear in blockchain and IoT systems as part of unique, anonymized tokens or temporary data references. These identifiers help manage complex networks of devices and transactions while maintaining security and privacy.
Conclusion:
Binopofizxoc is a machine-generated identifier commonly found in system logs, URLs, or error messages. While it may seem mysterious, it’s typically harmless and used for tracking, debugging, or internal software purposes.
However, users should exercise caution and verify its source to avoid potential security risks. As digital systems evolve, identifiers like binopofizxoc will play a crucial role in enhancing system integrity and cybersecurity practices.
Also Read:




